Introduction Privacy and Audit Everywhere
RightsVault addresses the privacy and tracking (or audit) requirements for electronic records wherever they go in the digital world. RightsVault can stand alone, but we believe it will be most useful when integrated with existing document or information systems. Assuming such an integration, we discuss privacy and tracking beyond and within system boundaries.
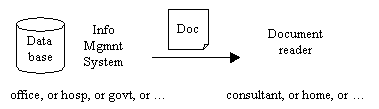 Most organizations have mechanisms for securing access to information within their information processing systems, but what happens when records are sent out to a recipient who is not running the same security system? Records are routinely sent between hospital and doctor, engineer and consulting engineer or client, lawyer or accountant and client, and between civil servants. When these records are in digital form, the potential for leaks and misuse is great. The results are embarrassing, damaging to business and career, and perhaps have legal ramifications.
Most organizations have mechanisms for securing access to information within their information processing systems, but what happens when records are sent out to a recipient who is not running the same security system? Records are routinely sent between hospital and doctor, engineer and consulting engineer or client, lawyer or accountant and client, and between civil servants. When these records are in digital form, the potential for leaks and misuse is great. The results are embarrassing, damaging to business and career, and perhaps have legal ramifications.
RightsVault secures and audits records, wherever they go whether or not the destination is intended, whether or not its in the same city or country. Legitimate users can use the records easily; unauthorized users cannot access them at all. All uses, even offline uses, are tracked for possible audit.
We do not claim perfect security. We claim superior security, plus auditability.
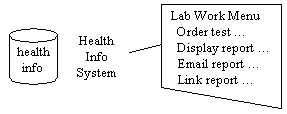 The same RightsVault mechanism that secures records outside the system can also be used to control the same records inside the system, as well as internal operations and access to specific data in a database.
The same RightsVault mechanism that secures records outside the system can also be used to control the same records inside the system, as well as internal operations and access to specific data in a database.
It can track operations on a finer scale, or more frequently, than it authorizes use. Authorization might be at a high level (e.g. can this user use this health information system at all? to access data for this patient?), then at a lower level only on specific operations or data accesses (e.g. can this user order HIV tests for this patient? display them?). Tracking might be turned on for many more kinds of data accesses (e.g. all types of test orders and test result accesses, send email).
This overview focuses mostly on security outside the host information processing system. This is the harder problem, and the one organizations need most help with. See section Deployment Over the Net below for a discussion of using a single RightsVault for internal and external authorization and tracking.
 Most organizations have mechanisms for securing access to information within their information processing systems, but what happens when records are sent out to a recipient who is not running the same security system? Records are routinely sent between hospital and doctor, engineer and consulting engineer or client, lawyer or accountant and client, and between civil servants. When these records are in digital form, the potential for leaks and misuse is great. The results are embarrassing, damaging to business and career, and perhaps have legal ramifications.
Most organizations have mechanisms for securing access to information within their information processing systems, but what happens when records are sent out to a recipient who is not running the same security system? Records are routinely sent between hospital and doctor, engineer and consulting engineer or client, lawyer or accountant and client, and between civil servants. When these records are in digital form, the potential for leaks and misuse is great. The results are embarrassing, damaging to business and career, and perhaps have legal ramifications. The same RightsVault mechanism that secures records outside the system can also be used to control the same records inside the system, as well as internal operations and access to specific data in a database.
The same RightsVault mechanism that secures records outside the system can also be used to control the same records inside the system, as well as internal operations and access to specific data in a database.