Deployment Over the Net
In this paper we use the word Net in preference to Internet, to emphasize that RightsVault is deployable over the Internet, and Intranets, and Extranets - any network of any scope as long as it uses Internet protocols for communication. The deployment shown in the first diagram in section Integrated System Structure above is typical, but many more configurations are feasible. Lets consider four examples.
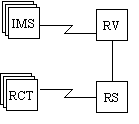 RightsMarket, or the Info Mgmnt System (IMS) supplier, runs co-located RightsVault (RV) and RightsServer (RS) installations for many small users of the Info Mgmnt System. Many end users of their protected docs run the freely available combination of RightsClient and Trusted Tool (RCT). Both server components might be on the same machine.
RightsMarket, or the Info Mgmnt System (IMS) supplier, runs co-located RightsVault (RV) and RightsServer (RS) installations for many small users of the Info Mgmnt System. Many end users of their protected docs run the freely available combination of RightsClient and Trusted Tool (RCT). Both server components might be on the same machine.
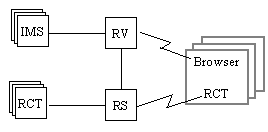 A large hospital or a regional health authority or an HMO runs all components, including many installations of the IMS and RCT. Outside users of protected hospital records can download from RV using nothing but a Web browser. Their RCT can communicate over the Net to RS to get permissions and track use.
A large hospital or a regional health authority or an HMO runs all components, including many installations of the IMS and RCT. Outside users of protected hospital records can download from RV using nothing but a Web browser. Their RCT can communicate over the Net to RS to get permissions and track use.
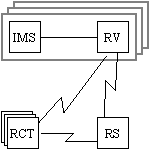 Several small and medium-size user ogranizations (e.g. small government (sub-)departments, small research facilities, labs, law firms, accounting firms, schools) each run their own RightsVault, but outsource the hosting of the RightsServer to RightsMarket or their IMS supplier.
Several small and medium-size user ogranizations (e.g. small government (sub-)departments, small research facilities, labs, law firms, accounting firms, schools) each run their own RightsVault, but outsource the hosting of the RightsServer to RightsMarket or their IMS supplier.
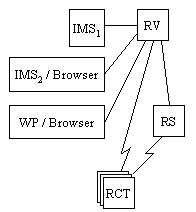 A large government department has many records systems and sources of information. It runs its own RightsVault and RightsServer to standardize the authorization and tracking mechanism for all systems and sources. IMS1 is fully integrated with RightsVault. Users of IMS1 secure and catalog its protected docs and set permissions through the user interface of IMS1. IMS1 operations (data accesses specfic to individuals, large order approvals, press releases, &) are authorized and tracked via RightsVault. IMS1drives RightsVault through RightsVault APIs.
A large government department has many records systems and sources of information. It runs its own RightsVault and RightsServer to standardize the authorization and tracking mechanism for all systems and sources. IMS1 is fully integrated with RightsVault. Users of IMS1 secure and catalog its protected docs and set permissions through the user interface of IMS1. IMS1 operations (data accesses specfic to individuals, large order approvals, press releases, &) are authorized and tracked via RightsVault. IMS1drives RightsVault through RightsVault APIs.
IMS2 is not integrated with RightsVault. Users export digital docs from IMS2 and then protect, catalog and set permissions for the docs through a Web interface to RightsVault. Some docs are simply typed up using a word processor (WP). These unprotected docs are then protected in the same way as the docs made by IMS2.
 RightsMarket, or the Info Mgmnt System (IMS) supplier, runs co-located RightsVault (RV) and RightsServer (RS) installations for many small users of the Info Mgmnt System. Many end users of their protected docs run the freely available combination of RightsClient and Trusted Tool (RCT). Both server components might be on the same machine.
RightsMarket, or the Info Mgmnt System (IMS) supplier, runs co-located RightsVault (RV) and RightsServer (RS) installations for many small users of the Info Mgmnt System. Many end users of their protected docs run the freely available combination of RightsClient and Trusted Tool (RCT). Both server components might be on the same machine. A large hospital or a regional health authority or an HMO runs all components, including many installations of the IMS and RCT. Outside users of protected hospital records can download from RV using nothing but a Web browser. Their RCT can communicate over the Net to RS to get permissions and track use.
A large hospital or a regional health authority or an HMO runs all components, including many installations of the IMS and RCT. Outside users of protected hospital records can download from RV using nothing but a Web browser. Their RCT can communicate over the Net to RS to get permissions and track use. Several small and medium-size user ogranizations (e.g. small government (sub-)departments, small research facilities, labs, law firms, accounting firms, schools) each run their own RightsVault, but outsource the hosting of the RightsServer to RightsMarket or their IMS supplier.
Several small and medium-size user ogranizations (e.g. small government (sub-)departments, small research facilities, labs, law firms, accounting firms, schools) each run their own RightsVault, but outsource the hosting of the RightsServer to RightsMarket or their IMS supplier. A large government department has many records systems and sources of information. It runs its own RightsVault and RightsServer to standardize the authorization and tracking mechanism for all systems and sources. IMS1 is fully integrated with RightsVault. Users of IMS1 secure and catalog its protected docs and set permissions through the user interface of IMS1. IMS1 operations (data accesses specfic to individuals, large order approvals, press releases, &) are authorized and tracked via RightsVault. IMS1drives RightsVault through RightsVault APIs.
A large government department has many records systems and sources of information. It runs its own RightsVault and RightsServer to standardize the authorization and tracking mechanism for all systems and sources. IMS1 is fully integrated with RightsVault. Users of IMS1 secure and catalog its protected docs and set permissions through the user interface of IMS1. IMS1 operations (data accesses specfic to individuals, large order approvals, press releases, &) are authorized and tracked via RightsVault. IMS1drives RightsVault through RightsVault APIs.